Cybersecurity is top-of-mind for anyone who uses VoIP systems. Protecting users against attacks is paramount. While some things may be out of your control, establishing an effective cybersecurity policy is an excellent way to ensure that the basics are covered, and to make it more difficult for attackers.
➤ Related Content: How to Convince Your Clients that VoIP Phone Systems are Reliable
We've put together an easy-start guide for creating an effective cybersecurity policy. Following these steps will create strong tactics and guidelines everyone in an organization can follow.
By the way - If you're a VoIP Reseller or MSP, you can use this guide yourself or copy+paste and send to your clients for their use. You have our permission to use the guide below as a free resource. You also have our permission to edit it to make it more relevant to your service. No credit for either is needed.
With that out of the way, let's get into the guide itself.
How to Create an Effective Cybersecurity Policy
1. Set a Password Policy
Eliminate any easy access points for malicious attackers by ensuring everyone is using a strong password. But you can't assume that everyone has the same understanding of what a strong password is. Create a password policy that everyone can use as a guide. Best practices include a safe place to store passwords - ideally, a password management tool, but definitely not a Google Sheet. Aim for long (but easier to remember) passwords. Historic advice is to create a password from a mix of symbols, uppercase and lowercase and special characters - but these methods are no longer as effective as a long password. Encourage users to make use of passphrases instead - strings of sentence-like words that are easier to remember. Ex: "Correct Horse Battery Staple"
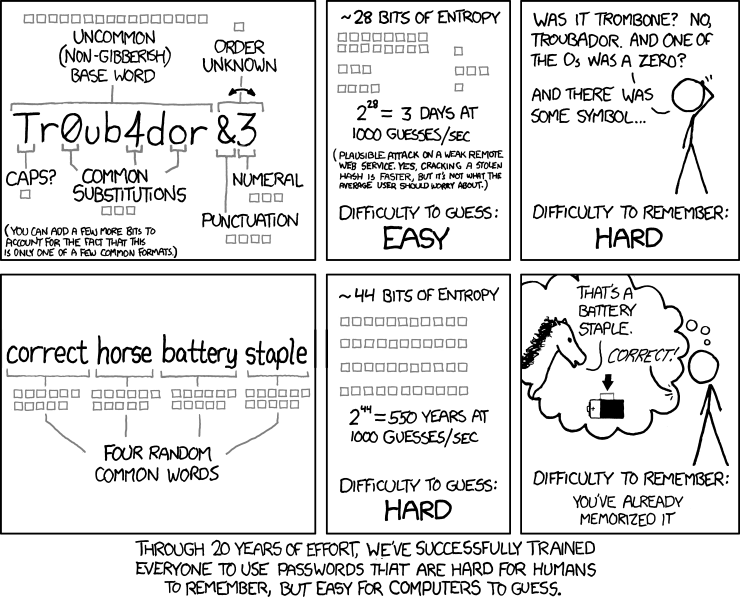
This comic from xkcd demonstrates how to create a passphrase
Additionally, require the use of multi-factor authentication wherever possible. This helps protect your systems further in the event of a password leak or hack.
2. Set Privilege Levels and Plans
Conventionally, access to systems and passwords is granted by seniority: employee has access to A, manager has access to A and B and boss has access to A, B and C. However - boss might only need access to B. The principle of least privilege is to grant user access based on what they need to complete tasks.
The logic of restricting access only to those who need it is that it eliminates extra entry points. This significantly reduces a business' security risk.
Likewise, you'll want to create a plan for deactivating old users. If someone leaves the company, their access should be revoked and they should be removed from the system. However, this is easy to overlook. Creating a plan for deactivating and removing users will ensure that this step isn't missed. If you're managing employees' devices remotely, that will allow you to update these access levels easily as well as revoke access as soon as necessary.
3. Call Evaluation
Tracking and storing call logs isn't just important for training and sales purposes - it's also an incredibly useful cybersecurity measure as well. Vishing - or call scams - are more and more common manipulation tactics designed to get users to hand over personal information. A common one is someone impersonating a person of authority - like an Amazon representative or IT employee - and requesting information to perform some task. These often sound legitimate and may even show a phone number associated with the correct business.
Using a call log dashboard, you can monitor call volume to keep an eye out for these out-of-the-usual calls. Recording them can also be used as an effective educational resource to show other employees what to look out for.
These tips will help you create an effective cybersecurity policy - either for your business or for your employees. Complex organizations may have more profound security needs, but these cover the basics that every organization should implement.
Not a Customer Yet?
➤ Request A Demo Of Our White Label VoIP Platform
Don't settle for 15%-20% sales commissions. Grow your business faster with the white label platform that allows you to achieve margins up to 70% - allowing you more control of your business.
About us: RingLogix offers a white label VoIP platform - RingOS - that enables Partners to sell, provision, invoice, and support their own branded VoIP and UC services. We make becoming a VoIP provider easy with a managed VoIP switch, instant order activations, hassle-free number porting, multiple services, and a flexible billing system.
_FBlogo_red.png)





